Brittle Script Automation
MDM scripts handle expected cases, then fail on real endpoint variation.
 PHARAOH
PHARAOH AUTONOMOUS ENDPOINT OPERATIONS
Agentic AI-driven IT operations designed to diagnose issues, remediate problems, and coordinate fleet-wide change at scale.
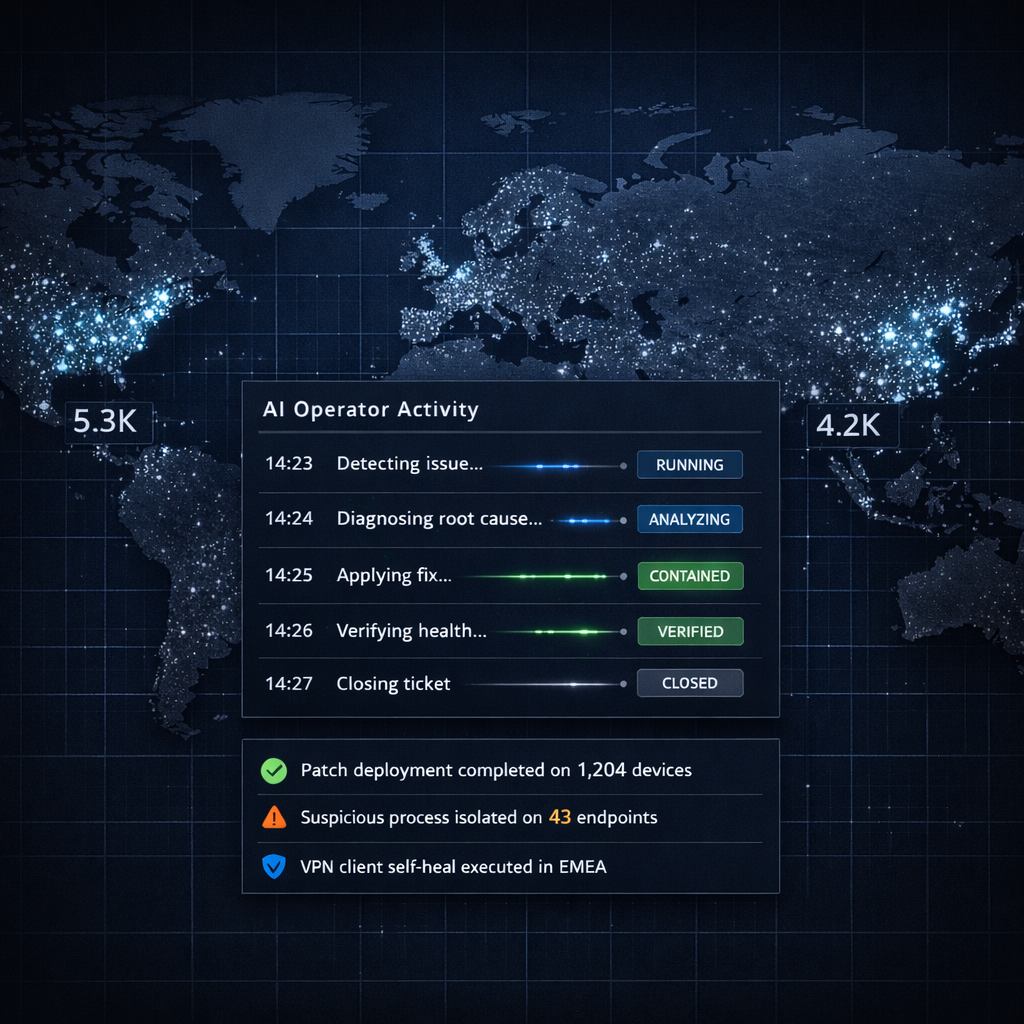
THE PROBLEM
MDM scripts handle expected cases, then fail on real endpoint variation.
Different OS versions, apps, and states break one-size-fits-all playbooks.
IT still spends hours triaging and repeating routine endpoint fixes.
Recurring employee issues keep cycling into the IT queue.
A common endpoint issue hits users across mixed devices and OS versions.
IT gathers context and picks a policy change, script, or one-off manual fix.
Traditional MDM actions handle some endpoints while edge cases return to queue.
Repetitive maintenance grows while proactive IT projects get delayed again.
Result: reactive support crowds out proactive IT operations.
Repeats daily
CORE CAPABILITIES
Pharaoh deploys an Endpoint AI Agent that can interact with apps, use PowerShell, write and execute code, analyze filesystem data, click through UI workflows, and verify real results on the machine itself — all within policy-defined boundaries and under operator control.
Traditional MDM pushes static scripts and policies. Pharaoh agents reason through the live state of each device and choose the best execution path in real time — within scoped permissions and approval workflows you define.
Pharaoh can:
Autonomous endpoint execution — scoped by policy, bounded by role, and auditable by default.
Agents investigate and remediate in parallel, so widespread endpoint incidents can be resolved in minutes instead of waiting in a human support queue.
At fleet scale, Pharaoh can:
Each agent retains machine-level facts such as location, network path, installed software, and prior successful fixes, so future troubleshooting starts with context instead of guesswork.
With knowledge and memory combined, Pharaoh can:
Collect logs, inspect filesystem state, and trace machine-specific root causes.
Execute shell/UI/code actions, verify outcomes, and escalate only true exceptions.
Apply policy-aware settings changes across fleets, even where no clean API exists.
WHAT TEAMS RUN TODAY
OPERATOR EXPERIENCE
> Run a forensic sweep for persistence mechanisms on all finance laptops.
> Prioritize hosts with unsigned startup binaries and isolate if confirmed.
> Generate an executive summary and technical incident report.Every action is logged, replayable, and policy-checked before execution. Humans stay in control; agents handle the repetition and scale.
SECURITY + GOVERNANCE
Security, oversight, and human control are foundational to Pharaoh — not afterthoughts. Every capability is built with governance in mind so your team stays in charge.
Role-based permissions, scoped execution boundaries, and approval workflows. Define what agents can and cannot do before they act.
Action trails, command transcripts, and evidence artifacts for every task run. Export logs to your SIEM or compliance platform. Configurable retention policies.
Operators can pause, override, or terminate any agent action at any time. Humans remain the final authority — agents never act beyond revocable delegation.
Autonomous behavior is constrained by risk tier and endpoint criticality. Actions are scoped per-endpoint with blast-radius controls — no lateral execution without explicit policy.
Agents operate with least-privilege credentials scoped to their task. SSO integration, revocable access per endpoint or group, and clear trust boundaries between agent and operator roles.
Data stays within your environment. Encrypted in transit and at rest. Deployment options support your data sovereignty and compliance requirements.
Cloud, private cloud, or on-prem patterns aligned with existing compliance needs. Agent binaries are signed and tamper-protected.
Built to support SOC 2, ISO 27001, and regulatory audit requirements. Structured evidence collection and change-control alignment from day one.
ECOSYSTEM FIT
Pharaoh augments your current tools rather than replacing them. It layers agentic execution on top of the management, security, and workflow platforms you already run.
Augments device management with agentic remediation that goes beyond static scripts and policies.
Resolves tickets at the endpoint layer so routine issues close without manual intervention.
Exports audit logs and action artifacts to your security monitoring and compliance platforms.
Connects with your identity provider for authentication, role mapping, and access control.
Surfaces alerts, escalations, and resolution summaries into the channels your team already uses.
Ingests your IT runbooks and documentation so remediation follows your procedures, not generic assumptions.
FAQ
Pharaoh augments traditional management layers with agentic execution. Instead of only running fixed scripts, it can reason through novel workflows and operate the same interfaces humans use.
Yes. You can define policy gates for actions like isolation, privilege changes, and software configuration updates before the agent executes them.
Pharaoh is built to ingest company-specific knowledge so support and remediation align with your environment, not generic internet assumptions.
No. Pharaoh increases throughput and response speed so IT teams can focus on complex decisions, architecture, and risk management.
Agents only access what their scoped permissions allow — such as logs, filesystem state, installed software, and configuration data needed for the task at hand. Data stays within your environment, is encrypted in transit and at rest, and is never used to train models. Retention and access policies are configurable to match your compliance requirements.
Operators can pause, override, or kill any agent action at any time. High-risk operations require explicit approval before execution, and blast-radius controls prevent any single action from affecting endpoints beyond its defined scope. Every action is logged with a full transcript so your team can review exactly what happened and why.
Pharaoh is in Design Partner Beta. We are working with a small number of enterprise IT and security teams to validate workflows, refine governance controls, and shape integration priorities before general availability. Design partners get hands-on access, preferred terms, and direct influence on the roadmap.
DESIGN PARTNER PROGRAM
We are partnering with security and IT leaders managing complex enterprise environments. Join early access to shape deployment workflows, governance controls, and integration priorities. Design partners receive preferred terms and direct input on the product roadmap.